
Products
Atakama Multifactor Encryption
Safeguard unstructured data against exfiltration
Data is the lifeblood of your organization, and should be protected from the threat of data exfiltration and ransomware at all costs.
Multifactor encryption is a progressive technology that leverages the power of advanced encryption with the proven security concept of multifactor authentication. Rather than focusing on protecting the systems or locations that store files, multifactor encryption protects at the individual file level, which is more secure and less resource intensive than the traditional encryption solutions and coupling data access to IAM, an approach that many organizations currently rely on.

Multifactor Encryption
Atakama’s unique approach to distributed key management (DKM) leverages threshold cryptography to split encryption keys and disseminate the key shards among multiple devices. Successful file decryption occurs only when the authenticated devices reconstitute the key.

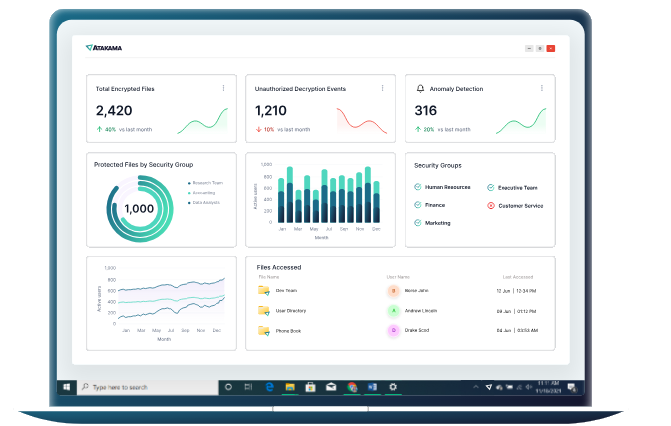
Intelligence Center
Provide data-driven intelligence for business reporting requirements, compliance, operational decision-making, and anomaly threat detection by visualizing, reporting, monitoring, and alerting on the status and location of your protected files, encryption events, and user activities.

Data Discovery and Classification Integration
By seamlessly integrating with leading data classification tools, Atakama helps organizations stay ahead of shifts in the modern threat landscape by automatically encrypting files according to policy defined by data classification.
SMBs bear the brunt of cyberattacks
Human error is a key driver in 82% of data breaches.
Source: Verizon.2022 Data Breach Investigations Report
Ransomware attacks up more than 95% over 2022
Source: Corvus 2023 Global Ransomware Report
The global average cost of a data breach in 2023 was USD 4.45 million
Source: IBM Cost of a Data Breach Report


Fight back against data exfiltration
Schedule a demo of Atakama’s Multifactor Encryption solution today












